Ajout d'un serveur à l'active directory
Prérequis
- Avoir un serveur linux
- Mettre les serveur active directory en tant que serveur DNS
- Mettre le domaine de recherche
- Avoir un nom de serveur respectant la bonne nomenclature
Installation des paquets nécessaire
- Installer le serveur de temps NTP:
apt install ntp - Paramétrer le serveur NTP
- Installer les paquets nécéssaire
apt install krb5-user libpam-krb5 libpam-ccreds samba winbind ntp - Paramétrer le fichier /etc/krb5.conf
[libdefaults] default_realm = MEGAPRODUCTION.LOCAL # The following krb5.conf variables are only for MIT Kerberos. kdc_timesync = 1 ccache_type = 4 forwardable = true proxiable = true rdns = false # The following libdefaults parameters are only for Heimdal Kerberos. fcc-mit-ticketflags = true [realms] DOMAIN.COM = { kdc = megaproduction.local # domain specific parameter (domain controller name) admin_server = megaproduction.local # domain specific parameter (domain controller name) default_domain = DOMAIN.COM # domain specific parameter (full domain name) } [domain_realm] .domain.com = MEGAPRODUCTION.LOCAL # domain specific parameter (domain name for dns names) domain.com = MEGAPRODUCTION.LOCAL # domain specific parameter (domain name for dns names) ~ - Paramétrer le fichier /etc/samba/smb.conf et y ajouter (en supprimant les doublons)
[global] workgroup = DOMAIN # domain specific parameter (short domain name) realm = DOMAIN.COM # domain specific parameter (full domain name) security = ADS encrypt passwords = true socket options = TCP_NODELAY domain master = no local master = no preferred master = no os level = 0 domain logons = 0 server string = %h server (Samba, Ubuntu) dns proxy = no log file = /var/log/samba/log.%m max log size = 1000 syslog = 0 panic action = /usr/share/samba/panic-action %d server role = standalone server passdb backend = tdbsam obey pam restrictions = yes unix password sync = yes passwd program = /usr/bin/passwd %u passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* . pam password change = yes map to guest = bad user usershare allow guests = yes - Joindre le domain
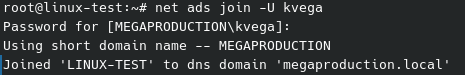
net ads join -U AdministratorRetour de la commande si tout se passe bien: